Primer: What your metadata says about you
In 2012, an officer violently arrested New York Times freelance photographer Robert Stolarik, allegedly for using a blinding camera flash during a street brawl in the Bronx, obstructing justice. But information associated with the digital photographs Stolarik snapped revealed that he hadn’t actually used his flash.
The officer, Michael Ackermann, was later arrested for fabricating facts and fired from the New York Police Department.
Metadata like the information found on Stolarik’s photos is created by and attached to all forms of digital communication, even encrypted messages. Its uses are far-reaching and, in some cases, vital. As former NSA Director Michael Hayden said in 2014, “We kill people based on metadata.”
It can also turn dead-end criminal investigations into convictions. In at least one case, metadata from call records alone contained enough information to convert an FBI investigation from 550 interviews that went nowhere into an ironclad conviction. FBI bomb expert Donald Sachtleben was sentenced to more than three years in prison for revealing information, including to the Associated Press, about a secret U.S. operation in Yemen in 2012. (Sachtleben was also convicted and sentenced to more than eight years in prison in an unrelated child pornography case.)
“It is really creepy how good a job the bad guys are doing of forging the email headers.” — Brian Reid, Internet pioneer, director of operations, Internet Systems Consortium
Every time you call your parents, slap a couple of emoji in a text or instant message, or send an email to your boss, you create metadata. And a person who accesses the metadata, even if indirectly or without your knowledge, can use it to figure key things out about you and what you have communicated—or to manipulate you.
An essential privacy threat
Not all uses of metadata are malicious or manipulative, although privacy advocates like those at the American Civil Liberties Union are critical of today’s ubiquitous collection and subsequent analysis of metadata.
German politician Malte Spitz, who in 2011 used a combination of personal metadata, public blog posts, and communication between his phone and cell phone towers to create a detailed map of his movements through the world, says widespread collection and analysis of metadata, whether sanctioned or clandestine, is threatening consumer privacy.
“We have an ongoing process where private companies try to get as much information as possible to profile and categorize people, not only through online information, but in every area of your life,” he told the digital and privacy rights group the Electronic Frontier Foundation in a 2012 interview.
“At the same time, government institutions are learning more and more that they don’t need to collect and store information,” he says, “since they can often gain access through private companies quite easily.”
Regardless of its potential threats to privacy, our most valued communication technologies cannot function without metadata.
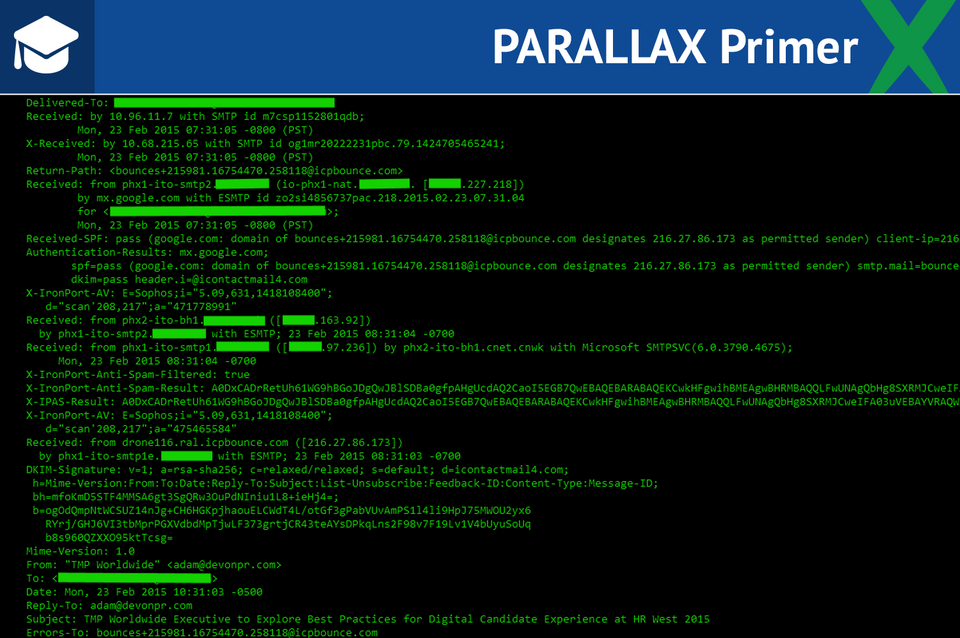
Email headers created by and attached to every email message (though often hidden by email program default) contain metadata detailing essential information such as the email addresses of the sender and recipient(s), the time and date the email was sent and received, the email client used, any Internet addresses that helped pass the message along its journey from origin to destination, and even the length of time it took to send the message.
Text messages, instant messages, and phone calls create similar kinds of metadata.
Someone examining your metadata records could determine when (and with whom) you prefer to text or talk on the phone, or whether you’ve attached a photo or a video to a message. And in theory, that person could map your metadata against your movements—which mobile phones constantly record, as they contact the nearest cell tower—to determine whether you were texting while driving, or even speeding.
Protecting yourself
Unless you’re an expert like Internet pioneer Brian Reid, currently director of operations at the Internet Systems Consortium, there isn’t much you can do to protect yourself, with respect to metadata. Despite being an essential element of our day-to-day communications, readily shared among interested parties such as data brokers and government agencies, metadata is often hidden or intentionally hard to access.
“Telecommunications companies have 100 years of keeping people away from that information,” and working with governments, not against them, Reid says. The long history of cooperation between telecommunications companies and government agencies has insulated them from prosecution. “They’re not about to give that up.”
You can examine metadata, in some cases, to protect yourself from phishers, who often manipulate basic email header information such as “from” addresses to con targets into clicking on embedded links, Reid says. By closely inspecting a message’s metadata, he usually can quickly determine its legitimacy.
“You can open it up and look at the actual transmitted data—see what’s there and what it’s claiming to be. I do this with every email that’s even slightly skanky,” Reid says. “It is really creepy how good a job the bad guys are doing of forging the email headers.”
Metadata from phone calls, text messages, or instant messages is harder to access and reveals less, Reid says. By viewing message logs, you can see some of it, such as time sent and number sent to, but the origins and communications routes of texts and calls are much harder to trace, even for experts, because doing so relies on specialized hardware.
You can also use technology designed to limit others’ ability to access your metadata.
In the wake of NSA whistleblower Edward Snowden’s document leaks, several companies have introduced mobile-messaging apps featuring end-to-end encryption. While services such as Signal and Wickr rely on metadata to ensure that their messages are properly delivered, they don’t retain it. This limits someone’s ability to snoop on your personal communications while protecting you from unwarranted data mining.
“Metadata alone is really all you need to know about what a person is doing,” Wickr co-founder Nico Sell told Passcode in October. “If you went to people and said that a government agency is keeping an activity log on every single thing they do throughout the day, most of them would not be happy with that arrangement.”
