Even North Korea has an antivirus program—but it’s used for spying
Malware and antivirus software usually go together like tacos and pickles. Leave it to North Korea to combine them like peanut butter and jelly.
Researchers announced on May 1 that when they inspected the ingredients of the North Korean antivirus software for Windows computers, they found a mix of spyware and old code stolen from an antivirus vendor.
The process that led to this discovery, publicly revealed on Tuesday, began in July 2014, when a pseudonymous source sent SiliVaccine 4.0 to the journalist Martyn Williams, who specializes in reporting on North Korean technology. And it ended a few months ago, after security researchers at Check Point Software, maker of the ZoneAlarm antivirus software, read a Bloomberg Businessweek story about North Korean hackers that linked to Williams’ research, and asked Williams to share the SiliVaccine file.
READ MORE ON SECURITY AND GEOPOLITICS
China evaluates vulnerabilities for attacks before disclosure
Tom Ridge on how we should fight our ‘digital war’ (Q&A)
Why Russia has a leg up in geopolitical hacking (Q&A)
How antivirus software could be used for government espionage
How Spain is waging Internet war on Catalan separatists
The researchers weren’t surprised, they told The Parallax, that SiliVaccine was rife with stolen code—in this case from a 10-year-old version of Trend Micro’s antivirus software. Williams and others have documented North Korea’s penchant for repurposing code, malicious and otherwise, without permission.
“The use of [Trend Micro] antivirus doesn’t particularly have a broad meaning. Pretty much any software can be targeted to be ripped off,” says Mark Lechtik, a security researcher on the Check Point Malware Research Team who led the investigation into SiliVaccine.
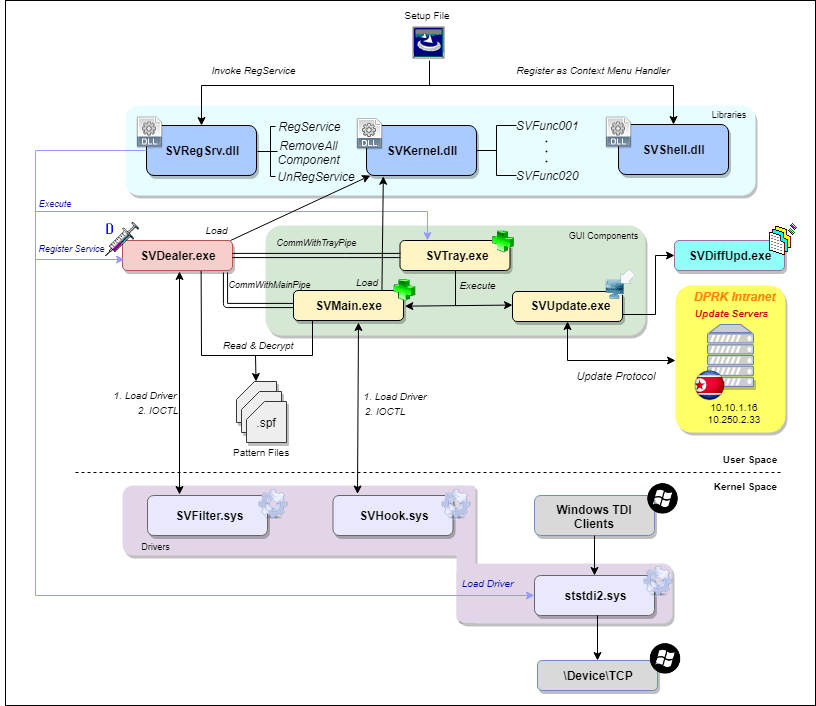
But finding that SiliVaccine was laced with the Jaku malware, which would enable North Korea to spy on the Internet activity of the users the software was ostensibly protecting, was enough to raise their eyebrows. They also discovered that it was programmed to ignore a malware programming characteristic that even decade-old Trend Micro code would have flagged as malicious.
Whatever the malware does, “the North Korean regime does not want to alert its users to it,” Lechtik wrote in his report.
Jaku is a known spyware-botnet combination, spread over BitTorrent. It has victimized an estimated 19,000 individuals, including journalists, and employees of government agencies, academic institutions, scientific organizations, engineering companies, and nongovernmental organizations.
The Thawte Certificate Authority issued a certificate found in the Jaku software to “Ningbo Gaoxinqu zhidian Electric Power Technology Co., Ltd.,” the identical name used to sign files by a group carrying out advanced persistent threats called “DarkHotel,” which has been attributed to North Korea threat actors.
Like many other countries, North Korea relies on its online prowess to advance some of its goals. The regime in Pyongyang has developed a group of an estimated 6,000 or more advanced state hackers, to whom experts have attributed notoriously aggressive operations such as the WannaCry attack of 2017, the $81 million heist of Bangladeshi banks in 2016, and the Sony Pictures breach in 2014.
It’s worth noting, Lechtik of Check Point says, that there’s a “discrepancy” between how North Korea portrays itself and how it acts on the global tech stage.
While North Korean officials project “into the domain of IT” that they are “trying to cooperate with the West, and work hand in hand,” Lechtik says, “they are at the same time doing these shady operations and [building] their products on shady practices.”
And because its interface is in Korean, there’s little doubt, says Michael Kajiloti, Check Point’s malware research team leader, that “SiliVaccine is targeted [at] North Korean citizens.”
Whether North Korean coders designed the software to spy on North Korean citizens living within the country’s borders, on the estimated 50,000 to 100,000 North Koreans who live outside its borders—or both—however, remains unclear.
North Korea greatly restricts its citizens’ access, physically and digitally, to the outside world. They have no global Internet access but rather a carefully curated intranet, Lechtik says. So why would Kim Jong Un want (or need) to spy on their Internet activity? And would he have reason to protect them via antivirus software from outside hackers or online exploitations?
“There is a phenomenon of smuggling media content into North Korea,” Lechtik says. North Korean citizens “are getting USB sticks or CDs with different kinds of media,” he says, “such as South Korean soap operas and TV shows.” And Pyongyang may well fear that smuggled foreign media is “an attack vector on their network.”
The unmasking of SiliVaccine’s origins underscores problems with controlling the computer code supply chain, says Leo Taddeo, chief information security officer at cybersecurity company Cyxtera.
“Threat actors use malware in general to collect information, and the various social-engineering techniques to implant that malware are common,” says Taddeo, who once led special operations at the Cyber Division of the FBI’s New York office. “We shouldn’t be surprised that this is yet another cyberattack tool that is masked as having a benevolent purpose.”
Kim Jong Un’s regime likely uses SiliVaccine to spy on North Korean expats, in addition to citizens living within the country, North Korea expert Bruce Bennett says.
“To spy on their people is the nature of North Korea,” says Bennett, the senior international and defense researcher for RAND Corp. He notes that life in North Korea is so restricted that it’s a criminal offense for North Koreans to partake of South Korean music and arts, something Kim Jung Un did in April with impunity, so it’s not surprising to him that Pyongyang would produce spyware masquerading as an antivirus program.
A “normal North Korean citizen” living in or visiting South Korea would have faced a minimum one-year prison sentence for attending a similar concert, Bennett says—not to mention for smuggling a recording of it into North Korea. Simply put, “Kim Jung Un doesn’t want outside information getting into the North.”
