Behind the chip on your credit card

Ever wondered what lies beneath that cool-looking chip on your bank card? What does it do? Why is it there? We’re going to dive into the magic of the EMV chip using my @monzo card as an example.
EMV is an acronym for the three credit agencies that contributed to its development in 1996: Europay, Mastercard, and Visa. (This was back when The Fugees’ cover of “Killing Me Softly with His Song” was really popular.)
The EMV chip is actually a really powerful computer. It helps cryptographically process payments, and it can store data. It works when you touch it against a contactless reader using near-field communication (NFC, which most Android devices and iPhones also use today) or insert it into a device (old skool, baby).
READ MORE ON PAYING SAFELY ONLINE
What’s the safest way to digitally pay?
Primer: How to protect your payment apps
How to send money securely
How to deal with Equifax and our ‘broken’ credit protection systemGive smart: 4 tips to avoid charity scams
Cybercriminals’ money-laundering backbone: Cash-strapped consumers
Primer: What’s in a banking Trojan?
‘Doom’ hack reveals more weak security in retail POS readers
How the chip manages its tasks is specified by two standards:
- ISO/IEC 7816 works for identification cards and integrated circuit(s) cards
- ISO/IEC 14443 works for identification cards, contactless integrated circuit(s) cards, and proximity cards
Sadly, these standards cost a fortune for independent developers to read—about $178—which impedes adoption. Standards should be open to all, not only to those who can afford them.
On the integrated circuit (IC), you’ll find a smart-card operating system (COS), which is a micro-operating system. For the electronic enthusiasts out there, this is how the pins look.

So what happens when you tap your card against, or stick it into, a reader when buying your morning coffee? First, the card activates, then it exchanges data for the transaction, and last, it deactivates.
Activation applies power to the chip on the VCC pin at a voltage determined by the specification, and the clock starts, running between 1Mhz and 5Mhz. It looks like this:
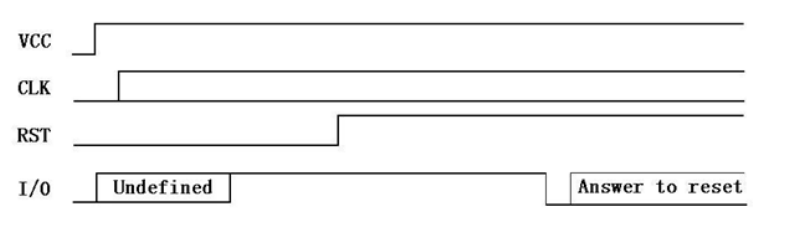
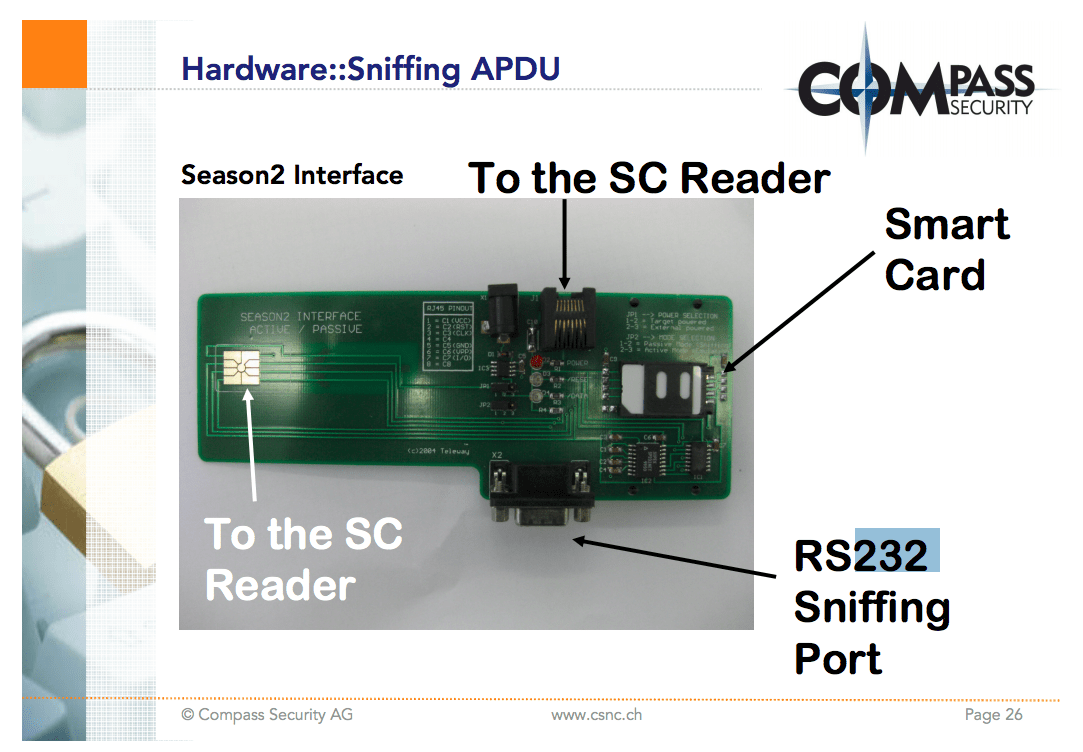
The chip uses application protocol data unit (APDU) to send data. Ivan Buetler, a researcher at Swiss computer security company Compass Security, gave a brilliant talk at the Black Hat conference in 2008 about this protocol that helped me understand how it works from a communication perspective (What happens when I tap my card? What low-level commands are sent and received?). He explained some of the possible ways to attack the protocol, such as sniffing the APDU communications channel using an RS232 (serial communication) hardware device. The example he gave was the Season 2 RS232 sniffer, commonly used in satellite TV hacking back in the day.
Your bank card’s EMV chip plays an important role in securing your transactions. With traditional magnetic stripe cards, the brown or black stripe has three tracks for storing data, but often, only two are used. Track 1 contains the bare minimum information for processing a payment. Track 2, which is smaller, holds such data as country code and your primary account number. These are read by the reader and are easy to copy—a feature criminals have regularly abused.
When you use a smart card equipped with an EMV chip at a retail location, by contrast, a unique, one-time transaction code is generated (and required). The bank then queries the card, checks that it is OK to use (including not reported as stolen or lost), and then allows the transaction. However, not every retailer accepts EMV transactions, so a fallback to swiping is still required for those instances. Around the world, 76 percent of transactions are now EMV-based.
EMV technology plays no direct role in online payments, which are classified as card-not-present (CNP) transactions. If I want to buy a new hat, I visit my favorite online haberdashery, choose one that suits me, and add it to my basket. I then click Pay Now, and enter my card details, which will be the 16-digit number on the front, the expiration date, and the card verification value (CVV) found on the back, into a form.
Once I click submit, the transaction magic happens over Secure Sockets Layer (SSL, which the cool kids call TLS these days), which means that it is encrypted to stop a site hacker from seeing and fraudulently using (or selling) that sensitive information.
When the website receives this data, it is supposed to ensure that it is handled in a secure manner. It typically is bound by PCI-DSS, the worldwide Payment Card Industry Data Security Standard, which was set up to help businesses securely process card payments and reduce card fraud. The website owner then sends the data, hopefully in an encrypted format, to a card processor (such as Worldpay), which handles the actual payment.
The online payment itself usually involves three stages: authorization, settlement, and funding. The processor takes my card details and sends it to the appropriate card association, such as Mastercard or Visa, which sends it to my bank to ask if it can authorize the amount. The bank checks the supplied CVV number and other details, then makes a decision of yes or no, and lets the processor know. This is all done within seconds, and the process is actually very secure.
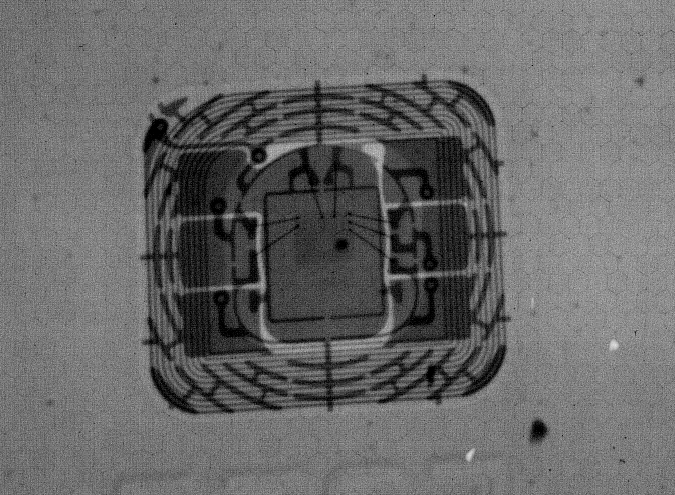
So what does this supercomputer physically look like? Above, you can see an X-ray of my @monzo card. You can see the coils of wire used to produce electromagnetic waves, which can then be picked up and turned back into current by another coil of wire. You can also see the bonding wires.
A lot of work is going into what the next generation of EMV chips look like, as our payment methods change. We are moving away from using plastic cards, and moving toward using more secure methods like Apple Pay, Google Pay, and Samsung Pay, which typically tie your phone’s NFC technology to your smart card, and are a lot more convenient to use for those who don’t wish to carry a wallet or a purse around.
These smartphone-based payment systems make use of a one-time unique token for each purchase, making it hard for unscrupulous characters to gain access to your card details. Add to the mix wearable innovations, such as the Mclear payment ring, and it’s apparent that there is currently a lot of research and development going into secure wearable payment devices.
As technology changes, and computing becomes smaller and more ubiquitous, we’ve entered an exciting time when it comes to payments and contactless transactions. But in order to keep our transactions safe, secure, and verified, we also have to be sure that we understand how the technology works and might be abused.
This column has been adapted and expanded by the author from his original Twitter thread on the subject.
