Exchange Server bugs could stalk health care for ‘months to come’
Thank you for subscribing to the free edition of the twice-weekly Parallax View newsletter. All issues are free through March 22. After that, you’ll receive one issue per week. If you’d like to support our independent journalism on the intersection of health care and cybersecurity with a paid subscription, you can do so here. If you'd like a subscription option not available, please email: seth@the-parallax.com.

While the global scope of newly acknowledged vulnerabilities in Microsoft’s Swiss Army knife-like Exchange Server impacts hundreds of thousands of organizations, health care organizations are especially susceptible to nation-state attackers in the months ahead—even after they’ve applied Microsoft’s patches.
That’s the consensus among cybersecurity experts who have been tracking the situation since it became public knowledge on March 2, when Microsoft announced that Hafnium, a previously unknown hacking group backed by the Chinese government, had been exploiting vulnerabilities in the tech giant’s widespread Exchange Server software. At the time of writing, at least one ransomware attack is suspected to have taken advantage of the vulnerabilities.
Microsoft’s Exchange Server is heavily used around the world, especially in enterprise and academic settings, to synchronize email among users. Many organizations use it to manage their mobile devices, as well as identities, contact lists, calendar events, and tasks across desktop computers and mobile devices. One of its most commonly enabled features is Outlook Web Services, or OWA, which lets users check their email from a Web browser.
The four zero-day vulnerabilities that Hafnium has exploited are particularly severe because they let the attackers install a Web shell. These bits of code create a backdoor to the server that could allow an attacker to read all email sent through the server, access other computers on the network, and gain full remote control of them.
Hafnium is not the only hacking group leveraging these Exchange Server exploits. At least 10 of these advanced persistent threat, or APT, families also have been using the exploit to hack Exchange servers, cybersecurity company ESET said in a blog post Wednesday. Independent cybersecurity researchers have begun to see proof-of-concept hacks that use these exploits to give them remote access and control of the servers.
“We’re concerned that there are a large number of victims,” White House press secretary Jen Psaki said March 5. The FBI and the Cybersecurity and Infrastructure Security Agency have published joint guidance on how to respond to the threat. CISA has created an Exchange vulnerability detection tool to help those who might be affected, and even the National Security Council has weighed in with a warning.
The United States has been the primary target of the cyberattacks, with at least 20,000—and possibly more than 60,000—affected organizations.
"There’s a substantial ransomware threat from these attacks.... It’s a very short trip to the rest of the network, if you’re starting from the Exchange Server." —Allison Nixon, chief research officer, Unit 221B
It’s hard to get a clearer picture of the number of impacted organizations, but at least two cybersecurity researchers have taken a stab at it. Cyberattack investigation company Unit 221B has built a Check Your OWA website to help organizations scan their Exchange servers for the vulnerabilities.
Allison Nixon, Unit 221B’s chief research officer, tells The Parallax that her company built the website to help organizations check their IP addresses and domains against a list it received of 86,000 affected IP addresses and domains. As of Thursday, 13.7 percent of the email addresses submitted, and 2.8 percent of the unique IP addresses observed, have been flagged as either "highly likely” or “maybe likely” to be compromised. These figures do not represent the total number of affected organizations, as there are some duplicates, and some organizations have dozens of Exchange servers.
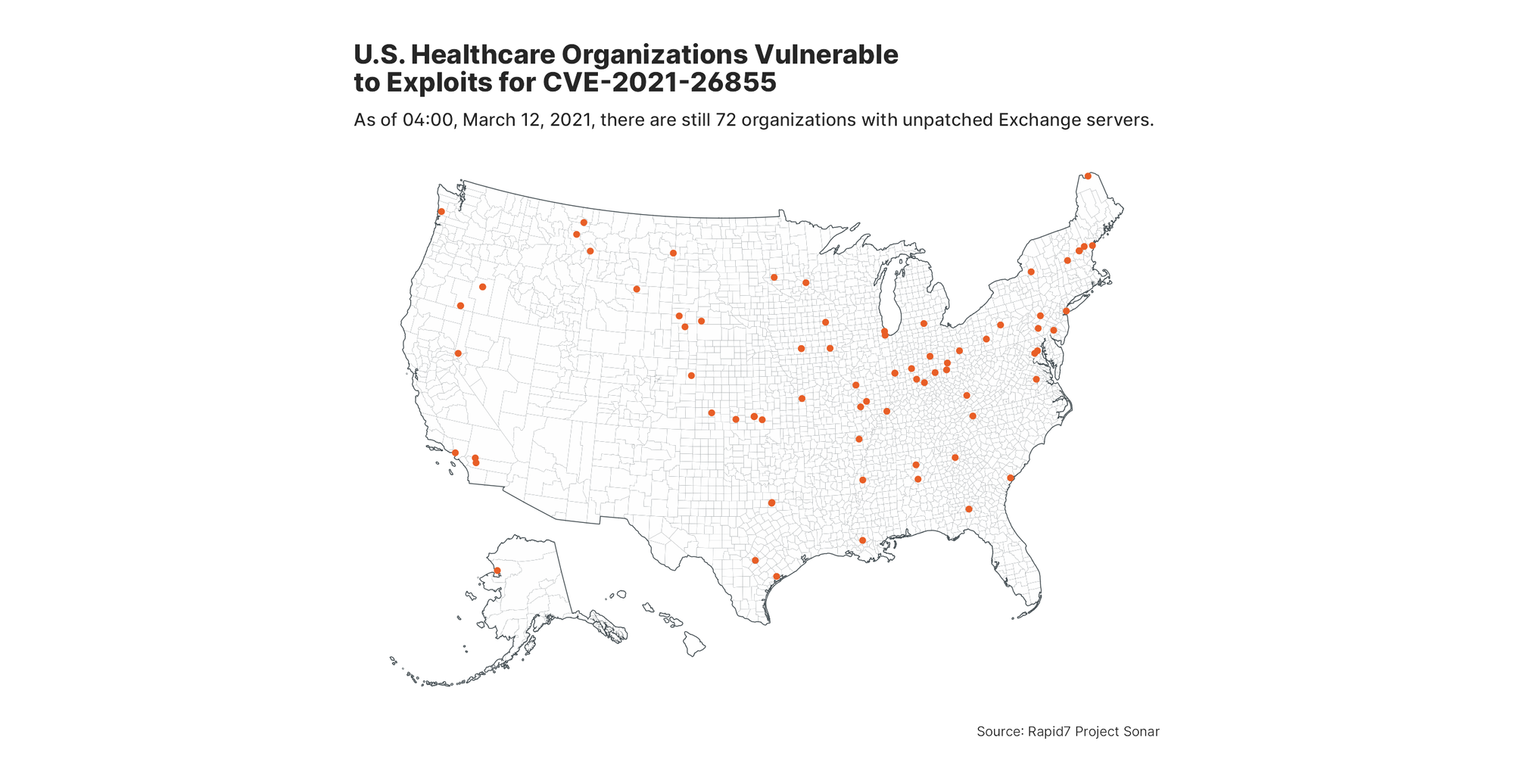
Separately, cybersecurity research and analytics provider Rapid7 curates a list of about 9,000 U.S. health care organizations that includes their domains and IP addresses. By cross-referencing a whole-Internet scan data provided by the company’s Project Sonar against its list of health care organizations and a separate list derived from its scans for vulnerable Exchange servers, Rapid7 was able to come up with a list of organizations that have yet to patch the Exchange vulnerabilities.
Bob Rudis, chief data scientist at Rapid7, pegs that number at 148 health care organizations, or 1.6 percent of the total from its custom list, as of March 7. By March 12, that number had dropped to 72.
Microsoft has released a software upgrade to patch the vulnerabilities a week earlier than expected, but that may not be enough to help protect some organizations, especially smaller health care-focused groups, warns Unit 221B’s Nixon. She says the full list of victims of these Exchange Server vulnerabilities is the “largest” she’s seen in her decade-long career.
“There’s a substantial ransomware threat from these attacks,” she says. “It’s a very short trip to the rest of the network, if you’re starting from the Exchange Server.” At the very least, smaller health care organizations should make a one-time backup of their systems, in case hackers have burrowed into their systems.
So far, that fear has yet to materialize, Errol Weiss, chief security officer of the Health Information Sharing and Analysis Center, said in an email to The Parallax. “Most” of the feedback the Health-ISAC has received so far from its members indicates that they are patching quickly, Weiss said.
“At this time, we're not hearing about any widespread successful exploitation in the health care sector, which could largely be due to the alerts we've shared, the seriousness [with] which IT teams are taking this issue, and the quick patching that's happening now,” he said.
"My guess, based on past events, is that we’re not going to see ransomware today or tomorrow, but we will see it down the road... We’re going to see the aftermath of these vulnerabilities for two to three months to come, if not longer." —Bob Rudis, chief data scientist at Rapid7
Still, affected health care organizations need to be hyper-vigilant in dealing with the Exchange Server vulnerabilities. They need to swiftly back up their data, disconnect the backup, search the mail server for installed backdoors, and migrate to either Microsoft's Office 365 or Google's cloud-based email solutions, Nicholas Weaver, a researcher at the International Computer Science Institute at University of California at Berkeley, said in an email.
The advised moves are “more feasible” for smaller organizations than large ones, he wrote. “The licensing costs for things like Google Workspace are on a per-user basis, so with a 100-person institution, it is close to 1/10th the cost of a 1,000-person institution.” Google and Microsoft offer HIPAA-compliant options, he added.
A lack of active exploits doesn’t mean that organizations that have patched their server software should consider themselves safe, says Rapid7’s Rudis. Not patching is risky for any organization, he says, but even those that do patch may not be completely safe.
“If you’re a good hacker, you’re not going to leave the Web shells on there for long,” he says. “They get on these systems, then move on to somewhere else in the organization. Many don’t have the resources or skill level or time to find all these incidents.”
He is also concerned that Microsoft’s update impacted not just current versions of its Exchange servers, but also older versions that it no longer updates. Organizations still running decade-old email servers are less tech-savvy and might be even more susceptible to cyberattacks, he says, because “they should’ve upgraded long before now.”
“My guess, based on past events, is that we’re not going to see ransomware today or tomorrow, but we will see it down the road,” Rudis says. “We’re going to see the aftermath of these vulnerabilities for two to three months to come, if not longer.”
Update, March 12 at 9:55 a.m. PST: Added latest number of unpatched U.S. health care organizations running Exchange Servers, according to Project Sonar.
A Tweet to live by:
All adult Americans will be eligible to get the vaccine no later than May 1.
— President Biden (@POTUS) March 12, 2021
What do you know that we don't?
Got a tip? Know somebody who does? You can reach us by email, Twitter DM, or Signal secure text: 415-730-3194.
Thank you for subscribing to the free edition of The Parallax View! Learn more about our paid subscription options here.
