How to use your Android as a 2FA key
MOUNTAIN VIEW, Calif.—Google just made it much, much easier for Android device owners to protect themselves with one of the safest extra security layers available to consumers. If you have a phone or tablet running Android 7.0 or later, you are a few steps away from turning it into a two-factor authentication key, the company announced at its annual I/O developer conference here on May 7.
Physical 2FA USB keys can be inserted into or tapped against desktops, laptops, tablets, or phones to create a coded, unique, one-time-only password as a second layer of authentication. They are considered to be more secure than two-factor codes sent by SMS or generated by apps, but many consumers have balked at paying $20 to $50 for an additional piece of hardware they’d have to carry around.
Google’s move to turn Androids themselves—the ones already in consumers’ hands—into the physical keys needed to unlock accounts is a “game changer,” Joseph Lorenzo Hall, chief technologist and director of the Internet Architecture project at the Center for Democracy and Technology, said in an email.
“It is much safer than one-time code systems, including SMS or authenticator code systems, as this is based on the FIDO 2.0 model, which uses separate keys for each origin and mechanically cannot respond to phishing sites that use, for example, a Cyrillic ‘a’ instead of the usual (Latin) ‘a,’” he wrote.
READ MORE ON ANDROID SECURITY AND PRIVACY
Android Q adds privacy, fragmentation
Google Play is an ‘order of magnitude’ better at blocking malware
Opinion: To stay safer on Android, stick with Google Play
Primer: Why are Androids less secure than iPhones?
How to FBI-proof your Android
How to wipe your phone (or tablet) for resale
For consumers who already have two-factor authentication set up, and are using it with a hardware key, Google has designed the Android 2FA key to work alongside other keys concurrently or as a backup—there’s no need to choose only one method.
As long as the Android 2FA phones are free of malware, they might even be more secure than separate two-factor authentication keys, such as YubiKeys, says Aaron Cockerill, chief strategy officer at Lookout Mobile Security.
“In fact, Lookout believes phones can be superior to keys because they can provide telemetry for continuous authentication that a key cannot—but, again, that phone has to be free from malware or other threats,” he said in an email. So far, separate hardware authentication keys are not known to be affected by malware.
Despite the extra layer of security that two-factor authentication offers, along with tech companies’ efforts to make it more accessible, consumers have not flocked to the technology. Adoption numbers vary across surveys: A Duo Security report from November 2017 estimated that only 28 percent of Americans use it; in January 2018, Google reported that fewer than 10 percent of Gmail users had set it up.
One could argue that no effort thus far has made the authentication technology as accessible as Google’s latest. By making consumer phones usable as a two-factor hardware keys, Google is ensuring that the 57.9 percent of Android owners running the more modern versions of the phone’s operating system are more secure—if they take a few steps to activate the hardware key and connect it to their Google account.
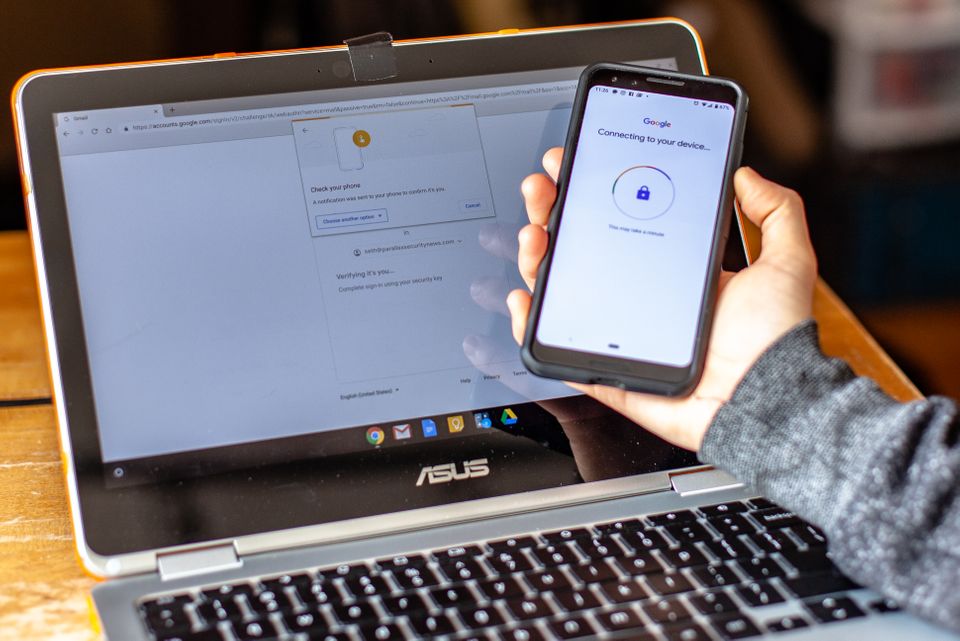
There are some limitations to using an Android device as the second factor in a two-factor authentication setup. First, as of right now, you can use it only with Google accounts. You must also activate Bluetooth connectivity and GPS location tracking on the Android device because the feature uses them to confirm proximity to the device you’re logging into.
Bluetooth must also be active on the device you’re logging into, though it’s important to note that Google says the technology does not establish a connection, or link, between the two devices beyond log-in authentication. Lastly, you need to use Google’s Chrome; the technology is not yet compatible with any other browser.
Google representative Sarah O’Rourke says that “in the future,” Google will add support for non-Google browsers and accounts. In the meantime, to set up your Android device as a second-factor hardware key for your Google account, you can follow these four steps.
Step 1: Ensure that you have set up a Google account on your Android phone. If you haven’t already done so, go to the Android Settings on your device. Choose Accounts, Add account, and then select Google.
Step 2: Ensure that you have two-factor authentication set up on your Google account. If not, go to Google’s two-factor authentication setup page, and follow the instructions. You’ll be asked to log in to your Google account and enter your phone number for SMS confirmation.
Step 3: On a laptop or desktop, open a Chrome browser, and go to myaccount.google.com/security. Click on “2-Step Verification.”
Step 4: Scroll down the list of choices for receiving the second key, and select “Add Security Key.” Your phone should be listed as an option. Select it.
Once you’ve completed these steps, a pop-up will appear on your Android 2FA phone when you log in to your Google account. Tap it to approve the log-in. You can also connect the phone over USB to the computer you’re signing into your Google account on.
For consumers who are skeptical about whether a hardware two-factor authentication key can actually protect accounts, Emily Schechter, product manager for Chrome Security, has a message for you: “Here at Google, there has never been a successful phishing attempt on a Googler since we implemented security keys,” a mandate for all employees since 2018.
Disclosure: Yubico provides The Parallax with our two-factor authentication YubiKey hardware.
