New research explores how the Great Firewall of China works
HAMBURG, Germany—It’s probably not a good idea to troll the so-called Great Firewall of China. It’s probably not a bad idea, however, to think about how do it.
At a presentation Sunday at the first day of the 32nd Chaos Communication Congress, the largest annual computer enthusiast and hacker conference in Europe, security researcher Philipp Winter presented details that he and his colleagues, fellow Princeton University researcher Roya Ensaf and University of California at Berkeley researcher David Fifield, have uncovered on how China’s notorious Internet censorship system works.
“Internet censorship tries to hide problems instead of grabbing them by the root,” Winter told The Parallax.
The firewall’s shifting nature makes studying it difficult. Difficult, but not impossible. During the course of their investigations into the firewall’s inner workings, the trio has uncovered some unusual behavior.
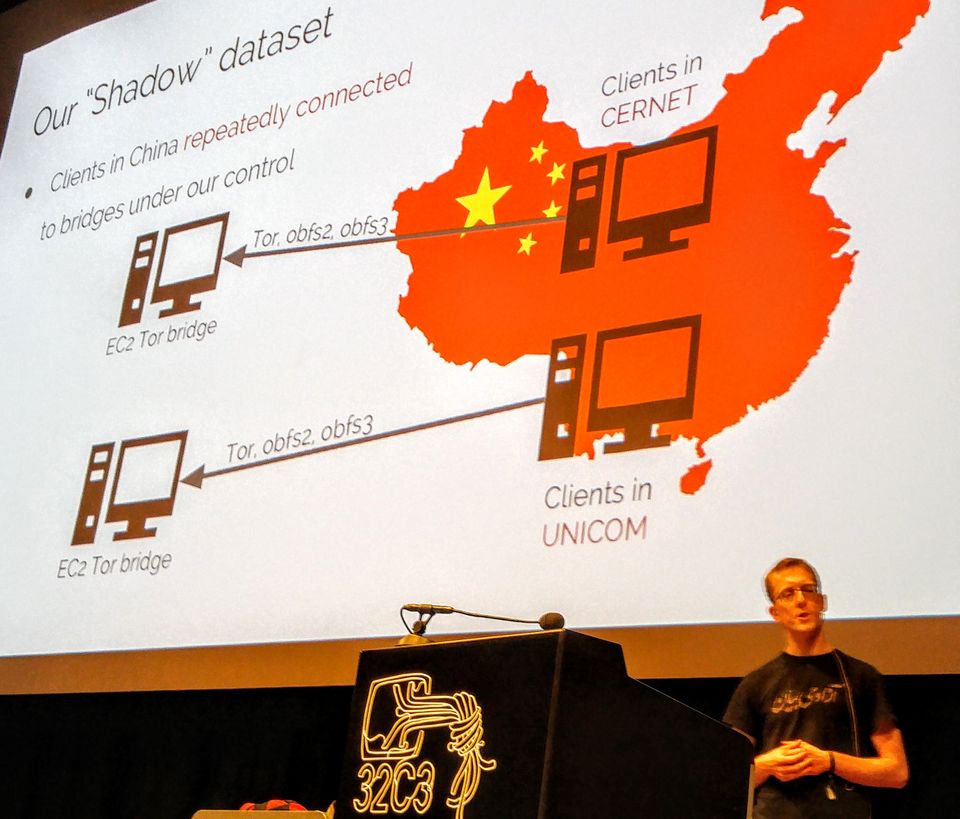
Cumulative research over the years has revealed the kinds of sites that the firewall blocks and how it blocks them, Winter said. Using surveillance techniques, the firewall detects content from foreign sites that people within China’s borders are attempting to reach, then blocks it from reaching their computers.
The Great Firewall also can detect coded traffic protected by encryption, thanks to a technique Winter and his colleagues describe as “active probing.”
But the Chinese government runs the risk of causing damage to its economy, if they block all encrypted traffic: What if the encryption is protecting financial data, and not political dissident communication? So active probing sends a probe to the foreign server that looks like a request for a connection to the anonymizing network called Tor.
“Every 25 hours, for a short time window, you’re able to connect to blocked IP addresses.” — Philipp Winter, security researcher
If it gets no response to the Tor request, it often will let the traffic through. But if the probe receives a Tor acknowledgement in response to the request, then the Firewall knows it’s a Tor communication and blocks it on the spot. Winter says the active probing and blocking by the Great Firewall isn’t limited to Tor (it also blocks commonly used encryption protocol SSH and SoftEther), but as a heavily used tool for political dissidents, Tor made a good example on which to present.
Active probing relies on a block of thousands of obscure IP addresses, Winter said. That makes it a highly unusual phenomenon in Internet traffic.
“Hand-crafting makes it possible for us to track the active probes,” he said.
Winter’s research documents that the probes, at least as they are currently constructed, fail on a periodic but regular basis.
“Every 25 hours, for a short time window, you’re able to connect to blocked IP addresses,” Winter said. “It’s not a massive finding, but it is interesting. I suspect they’re flushing [the firewall’s list of blocked websites] and then repopulating it.”
Despite what the researchers have learned about the firewall, Winter cautions that the firewall develops too rapidly for their findings to be used by large groups of people to break through it.
“Circumvention for a single person is not hard,” Winter said. “The hard part is to do it at scale.”
