NotPetya’s lesson for infrastructure: ‘Everything will be the new XP’
Critical infrastructure in Ukraine, and a smattering of systems around the world, from a hospital in West Virginia to a candy factory in Australia, last week were rocked for the second time in seven weeks by a rapidly spreading cyberattack.
The attack, originally identified as a resurrected variant of last year’s Petya ransomware, which locked computer data until a ransom was paid, turns out to have been worse: It deletes the data, too. Security researchers are now calling the attack NotPetya.
NotPetya deploys a wiper, a form of malware that “wipes out” the data on a computer or network. While wipers and ransomware may look similar, security researcher Matt Suiche explains in a blog post that they have different purposes.
“The goal of a wiper is to destroy and damage. The goal of a ransomware is to make money,” he writes. Ransomware can repair the damage it causes, but a wiper “would simply destroy [the data] and exclude possibilities of restoration.”
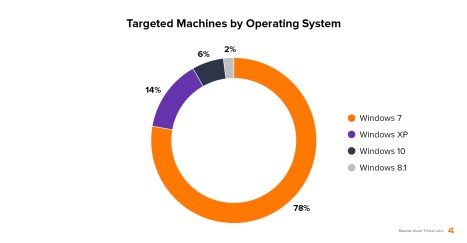
The exact origins and goals of the NotPetya attack remain shrouded in mystery, even after new demands appeared online a week after the original attack. It has glaring similarities to the WannaCry attack, a ransomware strike in May on an estimated 300,000 machines. They both targeted systems in Ukraine far more than those in any other country, but spread far beyond them. And they both exploited security vulnerabilities present in computers and networks running Windows 7 more than those running any other operating system.
The key differences: WannaCry isn’t a wiper. And NotPetya appears to have spread to only about a tenth as many machines.
While it’s tempting to blame the rapid spread of WannaCry and NotPetya on a notoriously hackable legacy version of Windows like XP, Beau Woods, deputy director of the Cyber Statecraft Initiative at the think tank Atlantic Council, says the critical security vulnerabilities we are seeing today are tied to far more than one outdated operating system.
“We’re going to have problems with Windows 7, Windows 10—even Windows 25, when it comes out,” Woods told The Parallax, as long as critical technology ranging from pacemakers to power plants are run on software lacking easy security updates.
“Everything will be the new XP,” he says, adding that in some cases, critical hardware is outlasting the software running it by decades. “Operating systems are expected to live 2 to 10 years; cars, medical devices, and industrial control systems will last 10 to 40 years.”
Today’s vulnerabilities are also tied to a growing number of traditionally “dumb” consumer devices connecting to the Internet, says Éireann Leverett, founder and CEO of Concinnity Risks, a computer security research and risk reduction company, who co-wrote a report published in May on the liability and longevity of operating systems.
READ MORE ON THE INTERNET OF THINGS
Critical systems at heart of WannaCry’s impact
Time for a Department of the Internet of Things?
The long reach of Mirai, the Internet of Things botnet
Hackers call for federal funding, regulation of software security
Shut the front door: The state of the ‘smart’ lock
5 questions to ask before buying an IOT device
Living on the edge of heartbreak: Researcher hacks her own pacemaker
Device security, Leverett says, “needs to be managed. Even when the manufacturer no longer exists.” And when manufacturers do exist but don’t address their security flaws, he says they should be held legally accountable.
“Liability would only affect those who don’t patch and don’t test, and [thus] produce harm.” Microsoft “shouldn’t be scared,” Leverett says, because it distributes security updates even for operating systems in use years beyond their service guarantee. Instead, he says, enforced liability would “cull the lazy polluters of the Internet.”
Beyond software and hardware vendors’ need to procure easily installed patches for their products, there’s a third place to point the finger: the widespread stockpiling and even brokering of vulnerabilities and exploits.
Until the hacker group ShadowBrokers leaked the Windows 7 security exploit that opened systems to the WannaCry and NotPetya infections, the National Security Agency had held it as a government secret to potentially use in its own cyberattack. Although Microsoft issued a patch for the flaw in March, two months before the WannaCry attack, the ransomware still managed to lock up hundreds of thousands of unpatched computers in a matter of hours.
Riley Eller, a longtime member of the hacker community and chief technology officer of Unium, which makes Wi-Fi router software, suggests moving more software—including the operating systems and firmware that power the ever-growing Internet of Things—to a subscription-based service, not unlike what Adobe Systems did with Photoshop in 2013. By doing that, Eller says, software vendors could more easily install security updates that block attacks like WannaCry and NotPetya.
But even if software makers provided easily (or even automatically) installed security updates, Eller acknowledges that many of today’s critical systems would likely remain vulnerable.
READ MORE ON RANSOMWARE
How to avoid ransomware—or remove it
Ransomware is ‘blood in the water’ for hacker extortionists
Why ransomware increasingly targets the little guys
Despite new risks, experts still recommend using antivirus software
“This is a consequence of using consumer-grade computing devices and not having a stronger [security] regime, like using Windows computers to run nuclear devices on submarines,” he says, referring to the revelation that some British nuclear submarines still run on Windows XP, Microsoft’s operating system from 2002.
And the remotely controlled software update model has its own set of drawbacks, Eller adds—particularly for individuals and government entities desiring independence from businesses.
“The unfortunate side of security vulnerabilities is that it pushes people to become more and more dependent on corporate security,” he says. And “if nations don’t want to become the property of corporations, they need to come up with standards that force a device to warn us before it becomes a weapon that can be used against us. It needs to fall off the Internet and not come back on until its firmware has been updated.”
